
Developed a real-time malware detection engine using behavioral analytics and threat intelligence feeds. Detected and blocked ransomware like LockBit and WannaCry during simulation tests with a 98% accuracy rate, reducing threat response time by 60%.

Created a threat detection framework by mapping adversary behavior to the MITRE ATT&CK framework. Identified and flagged suspicious lateral movement, privilege escalation, and persistence techniques using log correlation and SIEM automation.

Built an AI automation system using Agentic AI principles, combined with machine learning predictions from various algorithms. Designed workflows to make intelligent, autonomous decisions based on dynamic data inputs.
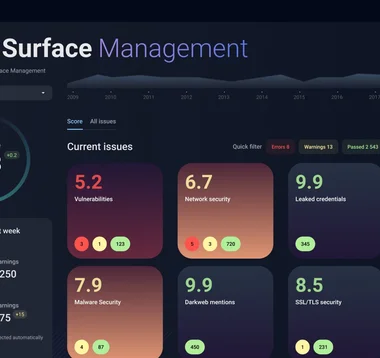
Designed and implemented an ASM dashboard that continuously discovers and evaluates exposed assets across cloud and on-prem infrastructure. Reduced critical exposure points by 75% through automated asset inventory, port scanning, and risk scoring.

Simulated Man-in-the-Middle and DDoS attacks in a controlled lab environment using tools like Ettercap and LOIC. Implemented mitigation techniques including SSL pinning, rate limiting, and Cloudflare WAF, effectively neutralizing attack impact in real-time.

Developed web and software applications using frontend and backend technologies. Implemented Agile methodology for efficient project management and streamlined software development.

Led an end-to-end forensic investigation of a compromised endpoint in a financial firm. Used Volatility and Autopsy to analyze memory dumps and disk images, uncovering unauthorized remote access, data exfiltration methods, and attacker entry point.

Designed cloud architectures and delivered cloud services using AWS and GCP platforms. Focused on providing secure, scalable solutions with strong emphasis on cloud security best practices.

Investigated a critical security incident by analyzing SIEM logs, endpoint data, and network flows. Identified misconfigured access controls and delivered a post-incident report with actionable remediations.